How Crypto Wallet Security Improvements Can Stop Most Scams

Crypto wallet security is more important than ever as scams continue to rise. When you hear about crypto scams, it’s easy to think, “This won’t happen to me.” However, in 2023 alone, an astounding $4.6 billion was lost to scams that crypto wallets can prevent.
One particularly alarming trend is the rapid rise of approval phishing scams, which saw explosive growth over the last two years. In 2023 alone, scammers stole an estimated $374 million by tricking users into visiting a website and approving malicious transactions.
Given the persistent threat of scams and the substantial damage they cause, identifying effective security measures is essential for the future of the web3 ecosystem.
For over a decade, we have been dedicated to researching crypto wallet security, and in the past two years, we’ve focused on testing crypto wallet security specifically in the context of web3 interactions. In this article, we demonstrate how secure crypto wallets can protect you from many common tactics used by scammers. We begin by explaining how secure wallets act as essential lines of defense against threats. Next, we put popular web3 wallets to the test against two real-world phishing attacks, revealing their pitfalls.
Why Secure Crypto Wallets Can Stop Scams
We see crypto wallet security as essential for protecting web3 users because most scams involve convincing victims to press the “Confirm” button in a wallet interface.
Malicious or Compromised dApps
The websites used by web3 phishing scams are malicious decentralized applications (dApps). A dApp runs on a blockchain network but has a web-based user interface or front end.
Crypto wallets can prevent scams by flagging interactions with malicious dApps and warning users of suspicious transaction requests.
Social Engineering
Beyond dApp-related threats, secure crypto wallets can also protect against social engineering attacks by detecting and blocking transfers to known fraudulent addresses, effectively stopping you from sending funds to scammers.
Which Crypto Wallet Security Features Can Protect You?
After extensive research on web3 wallet security and several attempts to standardize a crypto wallet security checklist, we have identified three security features essential for protecting users: Threat Prevention, Intent Verification, and dApp Permission Control. These categories emerged from our crypto wallet security testing project that resulted in reporting nearly a hundred security vulnerabilities in web3 wallets since 2022.
The Ideal of a Secure Crypto Wallet
In this article, we introduce the Secure Crypto Wallet concept, an ideal standard that represents the highest levels of wallet security features necessary to protect users from web3 threats.
From simple address blocklists to sophisticated transaction simulation, these crypto wallet security features serve as critical lines of defense against crypto fraud; let’s explore each of them in detail:
Threat Prevention
Some crypto wallets implement threat detection mechanisms that flag malicious web domains associated with known scams, serving as your first protective shield. As a next step, wallets also verify blockchain addresses to determine if they are linked to known scammers.
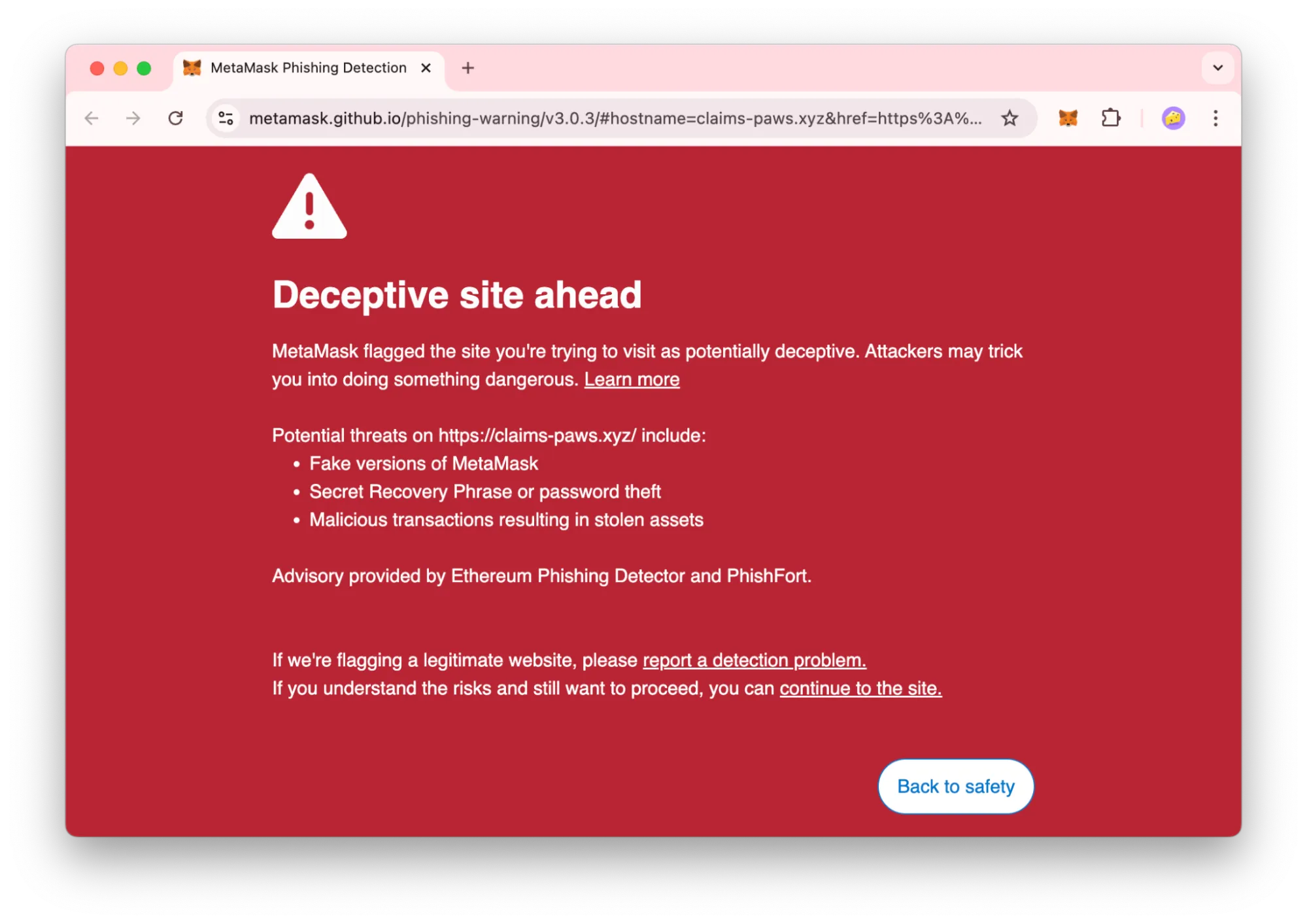
Intent Verification
Intent verification is the crypto wallet security feature that summarizes transactions in a human-readable way. If a phishing website is trying to steal your assets, a secure wallet can give you a clear heads-up, showing you the requested permissions or blockchain actions. For the most simple transactions you’ll be able to check immediately if something isn’t right.
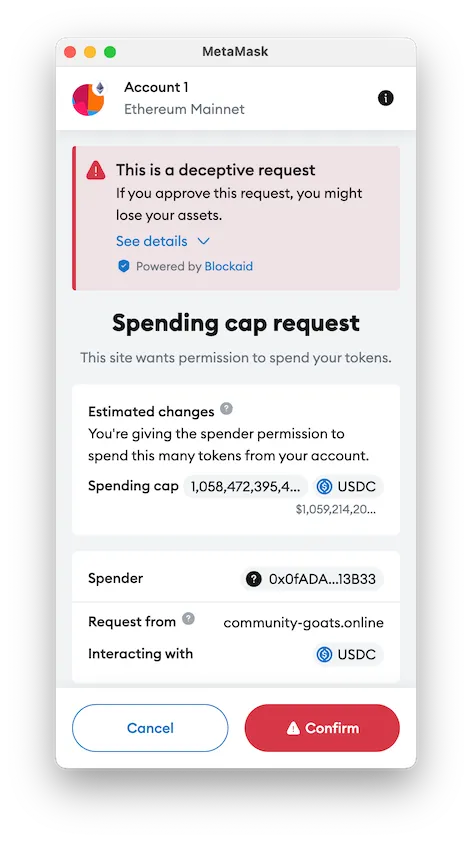
Transaction Simulation
Some wallets go even further, leveraging transaction simulation. This allows you to preview the potential outcomes of a transaction before it is executed, without affecting the assets. Transaction simulation previews show how the transaction will interact with smart contracts, including changes to token balances, fees, and other impacts on your accounts. Implementing effective transaction simulation is challenging, as demonstrated in this post.
dApp Permission Control
A secure web3 wallet will always ask for your permission before allowing a dApp to see your wallet balance or suggest transactions to approve. This way, you can always control which dApps are connected and can easily disconnect them. They also let you manage and revoke token approvals, giving you control over which contracts can transfer your tokens.
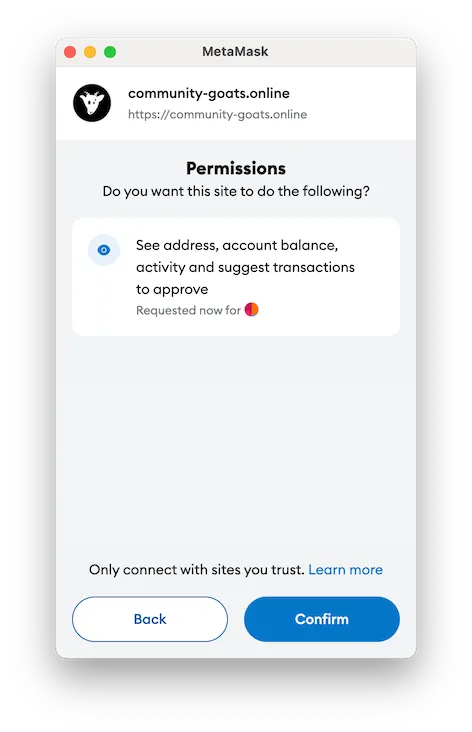
Scam Tactic: Fake Airdrops
You’ve probably seen this before: You’re scrolling through social media and spot a post announcing an “Exclusive Airdrop” from a popular crypto project. The offer seems simple: visit a website to claim free tokens or NFTs, with excuses like the following:
- “We are celebrating our 2nd anniversary with a special airdrop!”
- “Claim your compensation for a recent hack or network outage!”
- “This is your last chance to claim a huge token giveaway!”
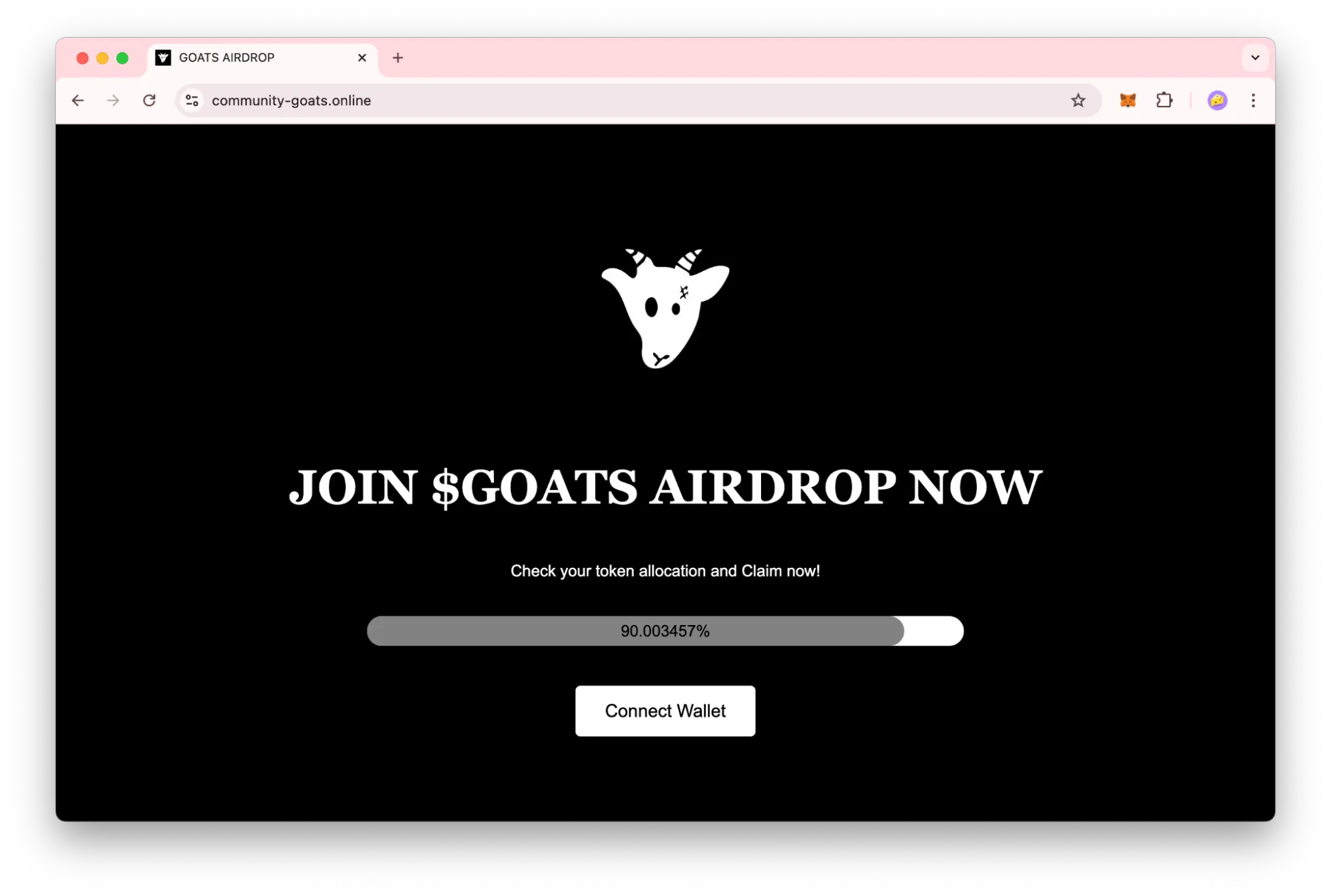
By clicking “Connect Wallet” in a malicious dApp, you’re granting it access to information like your wallet’s blockchain address and balance. More importantly, you are allowing the website to submit transactions for approval to your wallet.
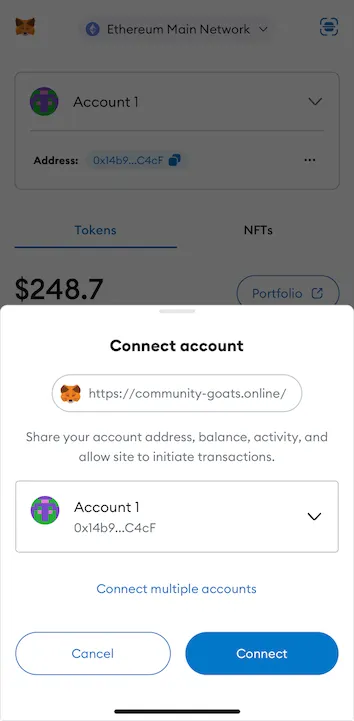
These websites are cleverly disguised phishing scams designed to gain access to your crypto assets. Once the web3 wallet is connected to the attacker’s dApp, they trick you into signing a seemingly innocent message, such as “Verify wallet ownership by signing this free message.”
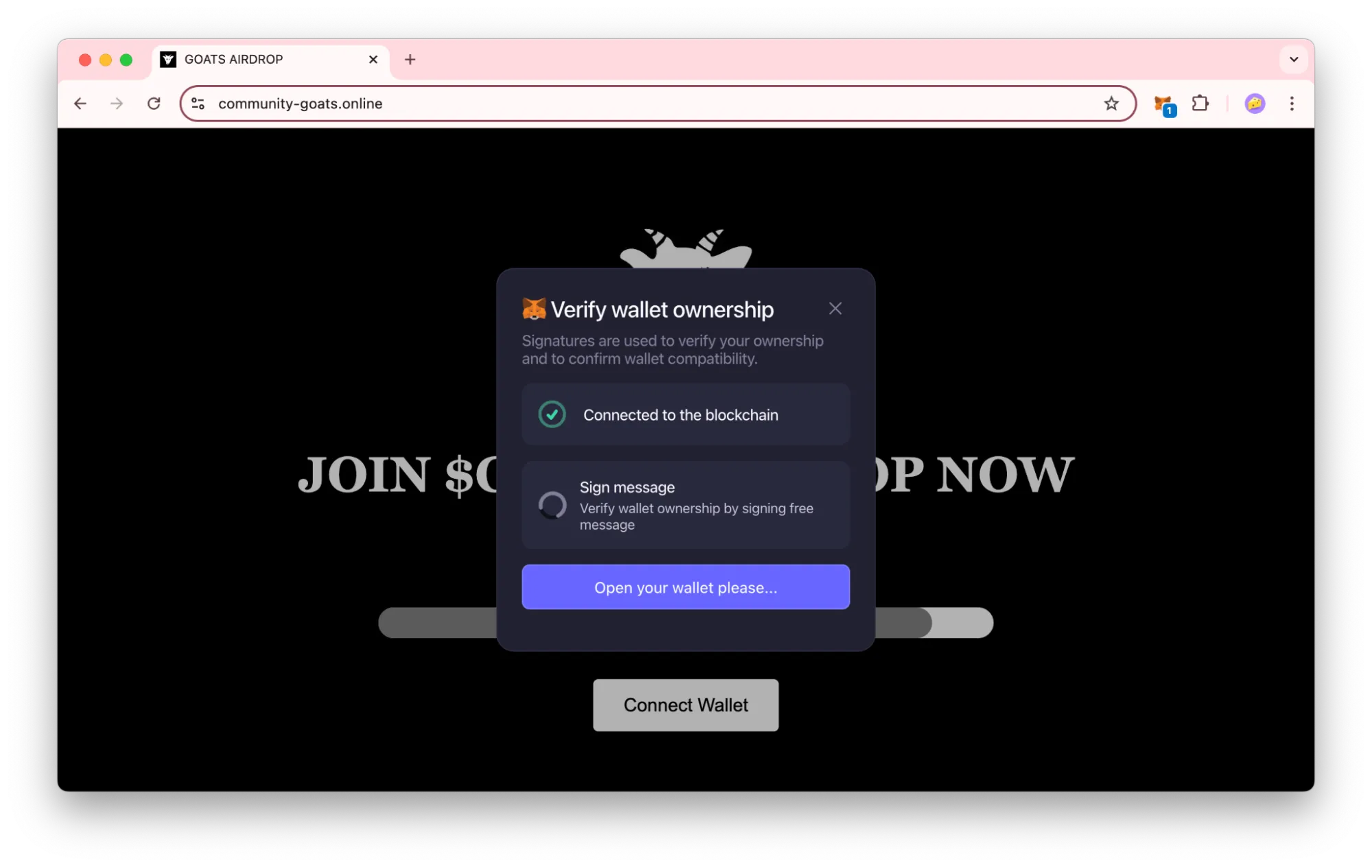
In reality, this disguised transaction is a spending approval request for a token from your wallet. The site asks you to use your wallet to sign a transaction where the “spender” (the contract or address that will have access to your tokens) is controlled by the scammers. It’s like signing a blank check—you’re granting the attacker unlimited access to your tokens. Once signed, they can drain your wallet, leaving you with no control over the outcome.
How Wallets Can Protect You
In this case, you are visiting a new dApp to do something you have not done before, this is not a widely-known dApp you and your wallet already trust. The features that can protect you are:
- Threat Prevention: The wallet can find the website address in a list of known malicious sites.
- Intent Verification: The wallet can clearly show that you are giving access to all your tokens to an unknown contract.
- dApp Permission: The dApp can’t submit signatures before approval and the wallet should provide clear and accurate information in the approval dialog.
What We Observed
- Blocklists of web and blockchain addresses are not updated as fast as necessary.
- Hard to understand or attacker manipulable confirmation dialogs.
- Spoofing and vulnerabilities in the user interface can allow attackers to manipulate what you see, tricking you into granting them permissions
Scam Tactic: Legitimate dApp Cloning
In this scam variation, the attacker creates a website that looks identical to a legitimate one—often replicating the design, layout, and branding of popular DeFi platforms. Even the domain name might be nearly identical, with only a slight variation, making it hard to spot the difference.
Think of it as going to your usual bank, except the cashier’s window has been replaced by a scammer, without you noticing. You still feel safe, as the bank building looks the same, but the person behind the counter is no longer legitimate.
You might stumble upon these fake sites through several channels: phishing emails or messages that link to the cloned site, compromised social media accounts of popular crypto figures or projects, or even by clicking on malicious Ads displayed as part of search engine results. These fake sites are designed to make you feel like you’re visiting a trusted platform, leading you to lower your guard and unknowingly provide access to your wallet.
One particular case of this scenario is when the official website is hacked, making the attack far more devastating. We’ll cover this in a future article.
When you connect your web3 wallet, these fraudulent dApp can attempt to get you to sign off on malicious transactions, just like in the fake airdrop scams. The excuses attackers use to convince you include:
- “Verify your wallet to participate in our new feature launch!”
- “Your account is temporarily locked—please log in to unlock your funds.”
- “Enter your seed phrase to recover lost funds from a recent hack.”
- “We noticed an issue with your recent transaction. Please contact support for help securing your account.”
As the site looks familiar and legitimate, you are often less suspicious and more likely to approve transactions or provide private keys. In any case, the outcome is the same: your funds can be drained once you sign. This method can be trickier for you to spot, because it leverages your trust in known platforms.
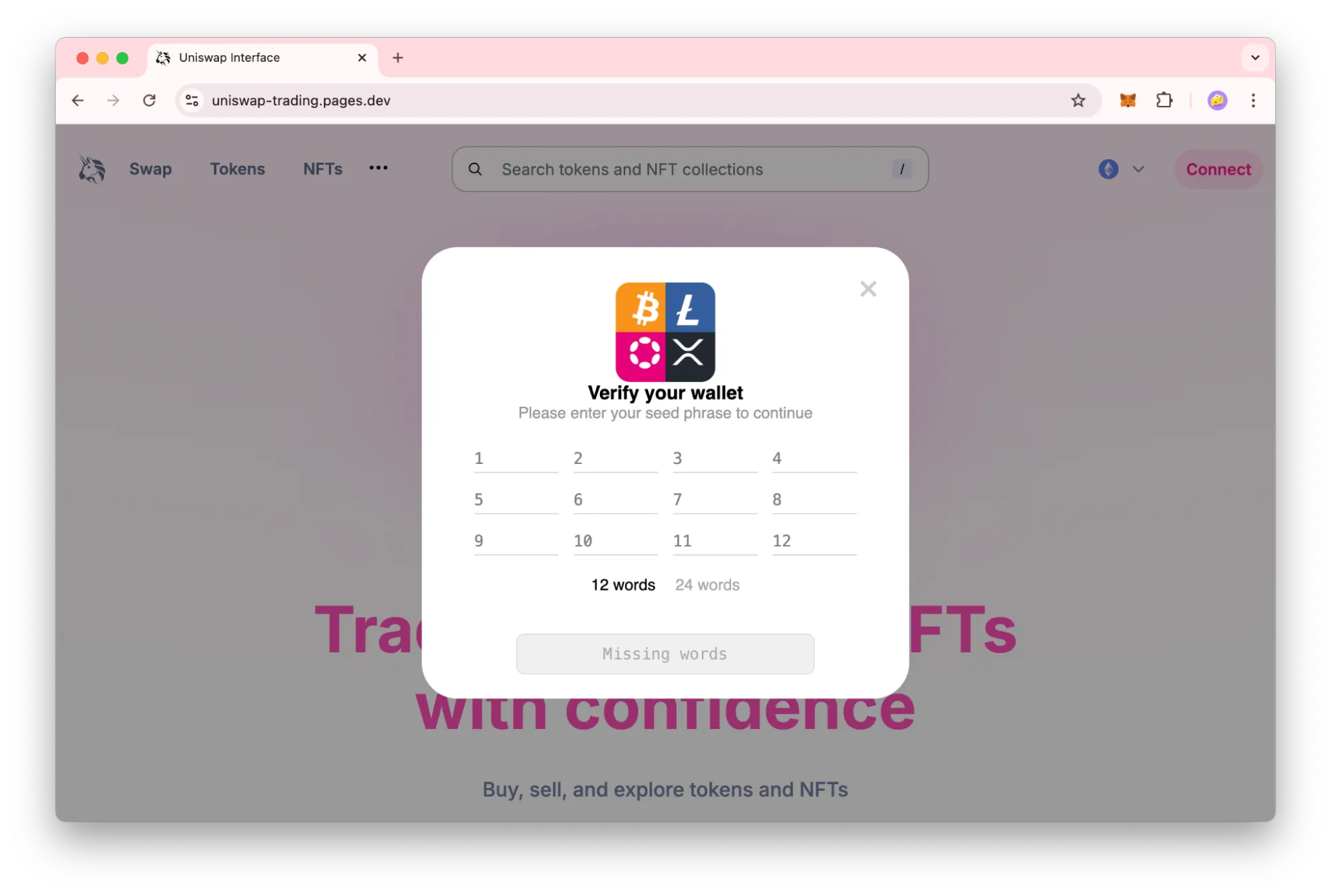
Some phishing sites prompt you to enter your wallet’s seed phrase, often under the pretense of account recovery or verification. Sharing your seed phrase grants full access to your wallet, and no wallet security feature can prevent subsequent theft.
However, we have observed scammers avoid this method because asking users to manually input their 12—or 24-word seed phrase is time-consuming and gives users a greater chance to recognize the scam and abort the process.
While wallets themselves cannot prevent you from willingly entering your seed phrase on a malicious site, wallet browser extensions could detect and block such sites using updated blocklists of known phishing domains. This approach, however, introduces privacy concerns, as it involves wallets monitoring user browsing activity.
How Wallets Can Protect You
In this case, you believe you are visiting a well-known dApp to do something you have done before, your wallet is probably already connected to the legitimate site but not to the cloned one. The features that can protect you are:
- Threat Prevention: The wallet can detect the website address that mimics a well-known DeFi dApp site. The wallet can have the website address and the blockchain addresses of the smart contracts for this app in a list of trusted addresses.
- Intent Verification: The wallet can clearly show that you are about to sign a transaction to interact with an unknown smart contract, probably deployed recently from untrusted sources.
- dApp Permission: The approval requirement is an additional step that can alert you about the discrepancies between the malicious site and the well-known site. In this dialog the wallet has the opportunity to show detailed info and alerts to help you discover the scam attempt.
What We Observed
- No attempt has been made by wallets to analyze the website content to identify new dApps that mimic well-known ones.
- Inconsistent intent verification implementations by the same wallet across the supported platforms.
- Vulnerabilities in the user interface help attackers mimic well-known apps.
Is Your Crypto Wallet Secure?
The analysis of the role of secure web3 wallets against phishing attacks and compromised dApps leads us to some intriguing questions:
-
Who is verifying these web3 wallet security implementations?
-
How frequently are resources such as threat prevention blocklists updated?
-
Are attackers bypassing the current web3 wallet security measures?
-
How can the average user decide which wallet offers the best protection?
The lack of clear answers unveils a critical oversight in the web3 industry: the absence of a standardized method for users to assess and compare the security levels of different wallets. Some wallets might have robust device locking but weak dApp permission controls, while others excel in threat prevention but fall short in transaction clarity. This disparity creates a confusing landscape for users trying to protect their assets.
Conclusion
As explored in this article, web3 wallet security is not just an individual concern—it’s the foundation of a trustworthy and thriving web3 ecosystem. While enhanced web3 wallet security features cannot stop all scams, prioritizing anti-phishing and other security features, web3 wallet vendors can significantly reduce user risk.
The need for an objective, regularly updated wallet security scoring system is clear.
At Coinspect, we’re committed to continually assessing and advocating for the highest standards in crypto wallet security and providing users with the tools they need to make informed decisions about protecting their Web3 life.