Want to get straight to the report? PDF is here.
Today, in coordination with the Tari team, we are making public Coinspect’s Tari security audit report. The audit lasted for 15 weeks and the document fully highlights Coinspect’s findings as well as Tari’s mitigation and updated status for all of the issues.
As a result of the Coinspect’s audit, 50 issues were discovered, with almost 50% of them being of HIGH severity and leading to double spends or massive denial of services for the network:
| Risk | Quantity |
|---|---|
| High | 22 |
| Medium | 9 |
| Low | 10 |
| Info | 9 |
Open Source Disclosures
During the audit process, Coinspect and the Tari dev team independetly found issues in the monero-rs library. Responsible disclosures were made to the project.
Out of excess of caution, the proof-of-concepts showing the exact exploitable paths for open source projects have not been included in the report.
Our L1 assessment process
Coinspect has longstanding experience working together with L1 teams to secure their chains. Through the years we have developed a process to understand the particular threats each chain faces, look for instances of these problems by reviewing the code and confirm them by executing reproducible proof-of-concepts which are shared with our clients.
For Tari’s scenario, we reflected part of our threat model in a diagram, which demostrates the kind of attack scenarios we were looking for when reviewing the codebase:
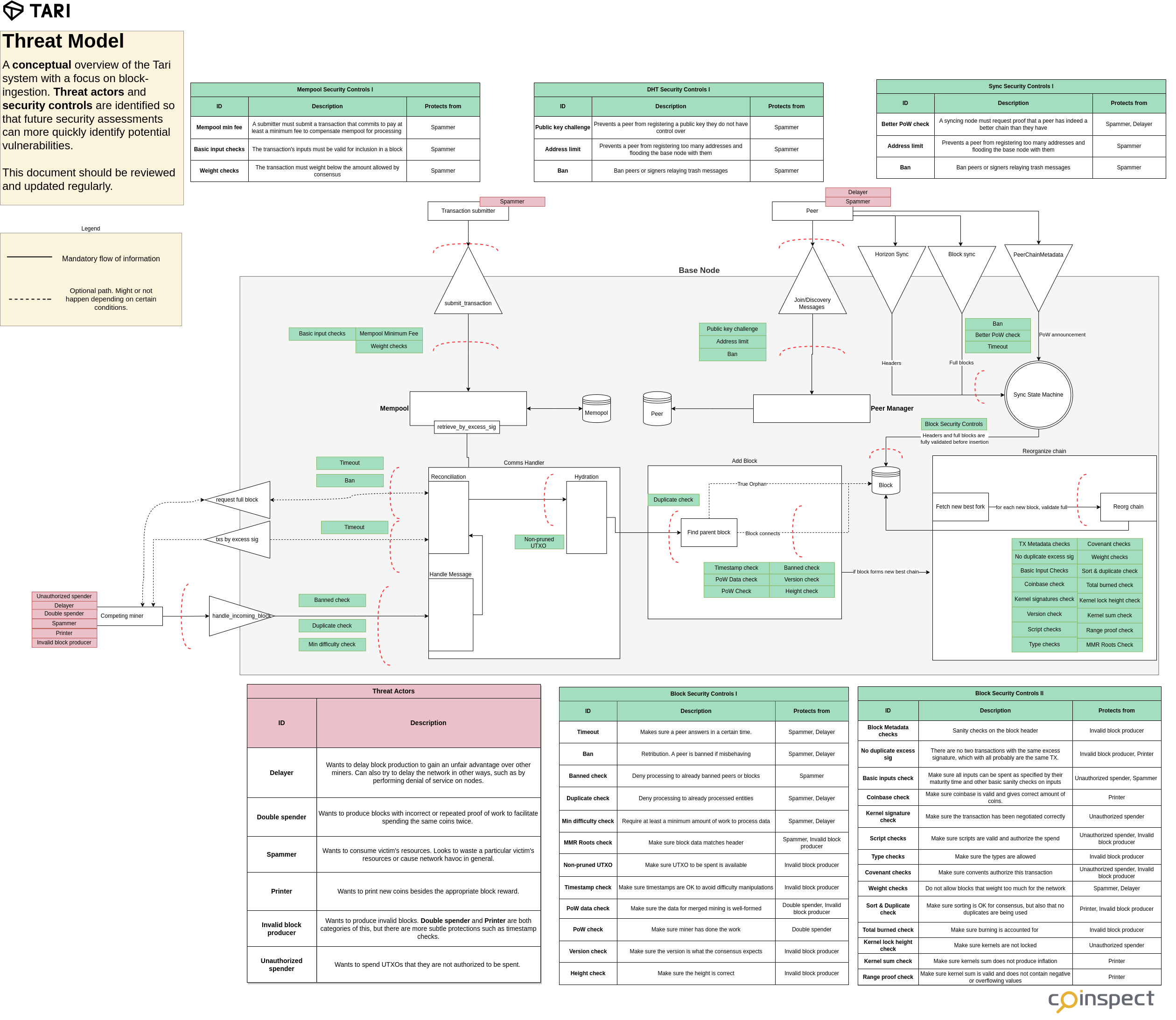
Expanding the public knowledge
Tari is a great example of a bleeding-edge blockchain with several features that make it an interesting case study with non-trivial vulnerabilities. That’s why we are making a series of posts using the results of the audits so that these issues are fully documented and are hopefully not repeated in other chains.
We will be releasing these posts in the near future. Stay tuned to learn more about the issues and how to protect against them!
Working with Tari
Interactions with Tari during the audit process were superb. The development team showed understanding of the issues encountered and promptly began the work to not only fix the reported issues but to implement recommended security policies such as fuzzing. They have shown that security is a top concern for them and are commited to continually decrease the risk for future users.







